Disclosure of Invention
The invention provides a method, a device and a storage medium for detecting the safety of the Internet of things, which improve the intelligent degree of the safety detection of the Internet of things, can actively detect the safety loophole of the Internet of things system, effectively reduce the attack threat, improve the system safety and ensure the safety of the Internet of things.
The invention provides a method for detecting the safety of an Internet of things, which comprises the following steps:
acquiring a first communication signal between a reader and a tag in a first Internet of things system;
reversely analyzing the first communication signal to obtain attribute information of the first communication signal;
inputting the attribute information into a security evaluation model to obtain a security evaluation result of the first Internet of things;
and outputting a safety detection report corresponding to the safety evaluation result, wherein the safety detection report comprises a safety risk level of the first Internet of things system and/or a risk coping scheme of the first Internet of things system.
In an embodiment of the present invention, the method further includes:
acquiring a test instruction input by a user;
and processing the attribute information of the first signal according to the test case corresponding to the test instruction.
In an embodiment of the present invention, the attribute information of the first communication signal includes:
potential destructiveness, reproducibility, availability, scope of influence, discoverability, physical cost of attack, time cost of attack, impact factor, and success rate of attack.
In an embodiment of the present invention, the security assessment model is a BP neural network;
the BP neural network takes the attribute information of the first communication signal as input and outputs a safety evaluation result of the first Internet of things; wherein the BP neural network has learned the safety evaluation results corresponding to the attribute information of different signals.
In an embodiment of the present invention, the risk coping scheme includes:
for the aerial frame, the anti-replay mechanism such as sequence number management is adopted;
and the data stored locally is encrypted or obfuscated.
In an embodiment of the present invention, the test case includes:
dos attack, sniffing attack, counterfeiting attack, identity authentication test, data tampering, key acquisition and card cloning.
The invention provides a safety detection device for the Internet of things, which comprises:
the system comprises an acquisition module, a first communication module and a second communication module, wherein the acquisition module is used for acquiring a first communication signal between a reader and a tag in a first Internet of things system;
the analysis module is used for carrying out reverse analysis on the first communication signal to obtain attribute information of the first communication signal;
the evaluation module is used for inputting the attribute information into a security evaluation model to obtain a security evaluation result of the first Internet of things;
and the output module is used for outputting a safety detection report corresponding to the safety evaluation result, wherein the safety detection report comprises the safety risk level of the first Internet of things system and/or the risk coping scheme of the first Internet of things system.
In an embodiment of the present invention, the method further includes: a processing module;
the acquisition module is also used for acquiring a test instruction input by a user;
and the processing module is used for processing the attribute information of the first signal according to the test case corresponding to the test instruction.
The invention also provides a device for detecting the safety of the Internet of things, which comprises: a processor; and
a memory for storing executable instructions of the processor;
wherein the processor is configured to execute the executable instructions to perform the method for detecting the security of the internet of things in any one of the above embodiments.
The invention also provides a computer-readable storage medium, on which a computer program is stored, which, when executed by a processor, implements the method for detecting the security of the internet of things according to any one of the embodiments.
In summary, the present invention provides a method, an apparatus and a storage medium for detecting security of an internet of things, wherein the method includes: acquiring a first communication signal between a reader and a tag in a first Internet of things system; reversely analyzing the first communication signal to obtain attribute information of the first communication signal; inputting the attribute information into a security evaluation model to obtain a security evaluation result of the first Internet of things; and outputting a safety detection report corresponding to the safety evaluation result, wherein the safety detection report comprises a safety risk level of the first Internet of things system and/or a risk coping scheme of the first Internet of things system. The method, the device and the storage medium for detecting the safety of the Internet of things improve the intelligent degree of the safety detection of the Internet of things, can actively detect the safety loophole of the Internet of things system, effectively reduce the attack threat, improve the safety of the system and ensure the safety of the Internet of things.
The foregoing description is only an overview of the technical solutions of the present invention, and in order to make the technical solutions of the present invention more clearly understood and to implement them in accordance with the contents of the description, the following detailed description is given with reference to the preferred embodiments of the present invention and the accompanying drawings.
Detailed Description
The technical solutions in the embodiments of the present invention will be clearly and completely described below with reference to the drawings in the embodiments of the present invention, and it is obvious that the described embodiments are only a part of the embodiments of the present invention, and not all of the embodiments. All other embodiments, which can be derived by a person skilled in the art from the embodiments given herein without making any creative effort, shall fall within the protection scope of the present invention.
The terms "first," "second," "third," "fourth," and the like in the description and in the claims, as well as in the drawings, if any, are used for distinguishing between similar elements and not necessarily for describing a particular sequential or chronological order. It is to be understood that the data so used is interchangeable under appropriate circumstances such that the embodiments of the invention described herein are, for example, capable of operation in sequences other than those illustrated or otherwise described herein. Furthermore, the terms "comprises," "comprising," and "having," and any variations thereof, are intended to cover a non-exclusive inclusion, such that a process, method, system, article, or apparatus that comprises a list of steps or elements is not necessarily limited to those steps or elements expressly listed, but may include other steps or elements not expressly listed or inherent to such process, method, article, or apparatus.
The technical solution of the present invention will be described in detail below with specific examples. The following several specific embodiments may be combined with each other, and details of the same or similar concepts or processes may not be repeated in some embodiments.
Fig. 1 is a schematic flow chart of a first embodiment of a security detection method for the internet of things of the present invention. As shown in fig. 1, the method for detecting the security of the internet of things provided by this embodiment includes:
s101: a first communication signal between a reader and a tag in a first Internet of things system is acquired.
S102: and performing reverse analysis on the first communication signal to obtain attribute information of the first communication signal.
S103: and inputting the attribute information into a security evaluation model to obtain a security evaluation result of the first Internet of things.
S104: and outputting a safety detection report corresponding to the safety evaluation result, wherein the safety detection report comprises a safety risk level of the first Internet of things system and/or a risk coping scheme of the first Internet of things system.
Specifically, when solving prior art at thing networking safety inspection, the security hole in the thing networking is hardly detected and found fast to the mode of the artifical customization of testing personnel and analysis, also can't satisfy diversified detection demand in the thing networking environment, lacks the hold nature to thing networking system global security performance, and intelligent degree when examining time to the safety of thing networking is not enough. According to the method for detecting the safety of the internet of things, the first communication signal between the reader and the tag in the first internet of things system is collected and reversely analyzed, the safety evaluation model is designed and realized on the attribute information of the reversely analyzed first communication signal, the safety evaluation result of the first internet of things is obtained, and finally the safety detection report corresponding to the safety evaluation result is output. The first internet of things system described in this embodiment is only an example, and in practical application, the first internet of things system may be composed of a plurality of readers and a plurality of tags, where the readers are used to read information of the tags, and the tags are used to store information and serve as transponders to authenticate users. It will be appreciated that each tag in the first system of things can be read by each reader in the system. The first communication signal may be a communication signal between any reader and any tag, or may be a set of communication signals between multiple tags and multiple readers in the first internet of things system.
Optionally, the method for detecting security of an internet of things in the above embodiment further includes: acquiring a test instruction input by a user; and processing the attribute information of the first communication signal according to the test case corresponding to the test instruction. Different test cases can be customized, and the first communication signal of the first internet of things is tested and analyzed from different safety requirements. It is to be understood that steps S101-S104 in the above embodiments are also a test case.
For example: fig. 2 is a schematic structural diagram of a device for implementing the method for detecting the security of the internet of things according to the present invention. The method is used for realizing the Internet of things safety detection method. Wherein the device comprises: functional module 1: signal collection and analysis, which is used for collecting and analyzing RFID protocol signals off line; the functional module 2: the safety test case is used for RFID safety threat combing and related test routine compiling; the functional module 3: the safety evaluation model is used for constructing and simulating the RFID safety evaluation model; the functional module 4: a control agent interface; the functional module 5: the automatic test is used for realizing the design of the automatic test flow; the functional modules 1-5 form a prototype system, and test and verify the safety of the actual Internet of things through actual scene test and verification. The device in this embodiment can be according to specific scene, after using the parameter of experimental data training model, can carry out safety inspection and the risk assessment work of thing networking according to the experimental result. After the device is subjected to machine learning, corresponding schemes corresponding to different security scenes and risk levels are obtained according to different security detection scenes of the Internet of things.
Specifically, fig. 3 is a schematic view of an operation flow of a device for implementing the method for detecting the security of the internet of things of the present invention, which is used for the device shown in fig. 2 to execute the security detection of the internet of things, and as shown in fig. 3, the operation flow of this embodiment includes:
(1) the user starts the main program through the program interface. In the main program, a user can select different test case combinations;
(2) after the user initiates the test, the relevant command is sent to the agent module. The agent module possibly calls monitoring or reader or label simulation functions of the RFID lower computer system according to different scenes of the test case;
(3) if the monitoring scene is adopted, the test case calls an RFID signal acquisition and off-line analysis module, performs area scanning on the possible frequency band of the RFID system to be detected, and monitors and retains the communication process;
(4) after the signal monitoring and the retention are finished, the monitoring module provides the retained data to an offline analysis module of the RFID system security, the data is decoded and analyzed, and related information such as an RFID signal air interface, protocol layer data and the like can be obtained and fed back to a user security test case;
(5) the user safety test case evaluates the safety test case result according to the returned decoding information;
(6) the automatic test flow runs a series of test cases through the automatic test script to obtain an integral test result and feeds the integral test result back to the safety evaluation module;
(7) the safety evaluation module constructs an attack threat tree according to an overall test result obtained by the automatic test process and performs overall evaluation on the safety of the system to be tested by combining a DREAD classification evaluation system;
(8) and the safety evaluation scheme generation module dynamically generates an evaluation result report according to the evaluation result and provides a basis for safety personnel to formulate a reasonable and effective safety protection scheme for the tested system.
Optionally, the security evaluation module in the above embodiment is configured to perform the security evaluation result of the internet of things obtained according to the attribute information of the communication signal in S103 in the above embodiment, and the security evaluation model is a BP neural network. The BP neural network takes the attribute information of the first communication signal as input, and outputs a security evaluation result of the first internet of things, wherein if the BP neural network learns the security evaluation results corresponding to the attribute information of different signals, a security evaluation report corresponding to the attribute information can be output to the attribute information of the first communication signal in a machine learning manner.
Specifically, the attribute information of the communication signal may include: for each attack path in the first Internet of things, the security influence factors comprise potential destructive Da, reproducibility R, availability E, influence range A, discoverability Di and attack physical cost CohAttack time cost CotInfluence factor SceAnd attack success rate. Inputting the attribute information into data to train a BP neural network, and dividing the data into a training set and a verification set, wherein the label of the data can be a risk grade obtained through expert analysis.
TABLE 1
FIG. 4 is a schematic diagram of a security assessment model structure of a BP neural network of the security assessment model of the present invention. As shown in fig. 4, if the number of nodes of the BP neural network input layer is related to the influence factor, the 9 attribute information are used as the network input layer neurons, i.e., the input variable x
1And x
9. The output layer consists of 3 neurons y
1、y
2、y
3Is 0 or 1, (y)
1,y
2,y
3) The constructed 0-1 sequences respectively represent the system security level. The system security may be classified into, for example, 5 levels, "000" for high security, "001" for higher security, "010" for medium security, "011" for lower security, and "100" for non-security. Regarding the selection of the hidden layer, the selection is performed by a step-by-step test method, and 2N +1,
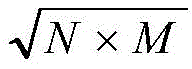
And finally finding out the most appropriate number of neurons of the hidden layer by using a common hidden layer selection method. Where N represents the number of input layer nodes and M represents the number of output layer nodes. It should be noted that before prediction, the BP neural network needs to perform learning training by using sample data, and the training mainly includes two processes: forward direction of informationPropagation and back propagation of errors. And inputting a verification set to verify the analysis result of the model after the training error is stable, and finishing when the error is stable. After the model is trained, the test set can be input, and then the system outputs the risk level of the RFID system. And if the risk of the system is high, a coping scheme of the system is given. Alternatively, the risk handling scheme in this embodiment may be one of the following tables: for the frame in the air, a playback mechanism such as sequence number management is adopted; and the data stored locally is encrypted or obfuscated. It is understood that other risk countermeasures listed in the examples of the present application are also within the scope of the present application. Specifically as shown in table 1 above.
Optionally, in the above embodiment, the test case may include, for example: dos attack, sniffing attack, counterfeiting attack, identity authentication test, data tampering, key acquisition, card cloning and other attack modes. In particular, the amount of the solvent to be used,
(1) lua, this requires invoking the associated device to send a high power channel noise interference reading. Returning a positive value by default, indicating that the attack is completed; and the command signal is sent continuously by the interference tag reply signal. The transmit carrier interferes with the dynamic range of the receiver.
(2) Sniff attack-sniff back false. UHF, manual participation is needed, and C # calls software 1 to leave the disk, analysis software 2-C # reads the disk-leaving file.
(3) A forgery attack-brutesim, which forges tag information to trick the commercial card reader to successfully read; if tag information can be read, then return true value, otherwise return false. Needs to work with a commercial test card reader;
UHF, reading ID, or reading storage area, needing to access key, possibly defaulting, or storing area;
c # calls test software-if the ID can be read, time stamping, and then listening to the file.
(4) Lua, the tester sends information to the tag to obtain id information. If the reading can be successfully carried out, the tag is encrypted, a true value is returned, otherwise false is returned.
(5) Data tampering writera: the tester forcibly writes a section of data into the tag and judges whether the data can be illegally written. If it can be written to and read from, then a true value is returned, otherwise a false is returned. UHF, ID, storage area may be modified.
(6) And acquiring a key, blasting the tag by using the dictionary by the tester, if the key used by the tag can be successfully acquired, returning a true value, and otherwise, returning false.
A default key is used, or documents have related cracking techniques.
(7) Cloning a card: the tester copies the card to the blank card by using the existing information and has the card function, if the card function is successful, the true value is returned, otherwise, the false value is returned.
Further, in the above embodiment, in the embedded software system security evaluation based on the threat model, the threat model is used as its basis to guide the implementation of the security test and evaluation of the system under test. The patent adopts a unified threat model theory to analyze and represent the security threats possibly faced by the tested system, and uses a threat tree to preliminarily describe the model. Firstly, defining basic concepts and terms related to a threat model, expressing and introducing the adopted threat tree, and then adopting a STRIDE classification method to identify the security threat faced by the tested system. And then, carrying out specific threat analysis on the system to be tested to finally obtain a complete threat tree of the threat model of the system to be tested.
The STRIDE threat classification model is a modeling model for threat analysis, which was first proposed and used by Microsoft corporation. The STRIDE classification model considers that the analysis of security threats can be considered from the following six aspects, as shown in Table 2:
TABLE 2
The STRIDE is the first letter of six threat types of disguise, tamper, repudiation, information disclosure, denial of service, and authority promotion. The STRIDE is considered to cover all security threats possibly suffered by the system, and is a relatively mature security threat classification model. In the embodiment, the security threats suffered by the tested system are classified by using a STRIDE method, and the six aspects are used as nodes of a threat model to construct respective sub threat trees, so as to finally form the threat model of the tested system.
FIG. 5 is a threat model structure of a system under test according to the present invention. As shown in fig. 5, the security assets of the tested system can be roughly classified into three categories, namely identity, protected data and authority, and the correspondence relationship between the security assets and six categories of threats in the STRIDE classification model is shown in table 3:
TABLE 3
Starting from six threat categories in the STRIDE classification model, establishing root nodes of various threat trees, and obtaining each threat tree of the tested system threat model according to the security asset and threat correspondence table. According to the definition of the threat tree in the threat model, each threat tree leaf node of the tested system threat model is a specific attack process. The backtracking path from a single leaf node to the root node of the threat tree is a possible attack path of the security threat of the tested system. Based on the attack paths, attack paths of each threat tree of the tested system can be obtained, and a safety test sequence suitable for the tested system is generated.
In the safety test activity, the evaluation of the safety of the tested system according to the test result is an indispensable important link. In this embodiment, a DREAD evaluation system is used to perfect a threat model of a system to be tested, and the security of the system to be tested is evaluated according to the threat model of the system to be tested. Specifically, for the security test of the system, the work of establishing a threat tree is used for analyzing and determining which aspects of security threats the tested system may suffer, and the security assessment work of the system determines the degree of damage of the security threats to the system and the difficulty and ease of utilization of attackers, so that a basis is provided for security personnel to make a reasonable and effective security protection scheme for the tested system. In this embodiment, two evaluation methods, namely a DREAD classification evaluation system and an attack cost/probability evaluation method, are adopted, and a security evaluation scheme of a tested system is analyzed and designed by combining a tested system threat tree and respectively starting from the two aspects of the damage degree of the security threat of the tested system to the system and the difficulty degree of the tested system threat to be utilized by an attacker.
The DREAD classification evaluation system is a security classification system used by microsoft and considers that any security threat can be evaluated in terms of its Potential destructiveness (dam Potential), Reproducibility (Reproducibility), availability (availability), impact ranges (Affected Users), and Discoverability (Discoverability). Each assessment aspect may be classified into 10 levels of 0-9, where a level of 9 indicates that the currently assessed threat may cause the most serious damage to the system in the assessment aspect, and a level of 0 indicates that the currently assessed threat cannot cause any damage to the system in the assessment aspect. It should be noted that, since the system under test does not include the user management part, and all operations thereof are differentiated by the authority of the operator, when the system under test is evaluated for threats by the DREAD classification evaluation system, the influence range of the threats is judged and analyzed by the influence on the role identities of the users. The evaluation aspects define criteria for damage caused by threats, such as the DREAD classification evaluation system described in table 4:
TABLE 4
The DREAD classification evaluation system provides a judgment standard for analyzing the system hazard degree of a single threat, and evaluates each specific threat in the tested system threat tree (namely each leaf node of the threat tree) by the evaluation system to obtain the threat weight of each specific threat. Because each threat node has an affiliation with its father threat node, the threat weight of its father node is mainly determined by its subordinate child nodes. In a tested system threat tree represented by an AND/OR tree, a parent threat node threat weight value has two value-taking modes according to the logical relationship between nodes under the jurisdiction of the parent threat node threat weight value. The set of weights S ═ Da,r, E, A, Di, wherein Da represents a potentially destructive threat weight; r represents a reproducibility weight; e represents the availability weight; a represents the weight of the influence range; di represents a discoverability weight. Setting parent threat node threat weight value set as f child node threat weight value set as that in the state that the subordinate child nodes are connected by AND logic, the parent node threat weight value can be represented by formula
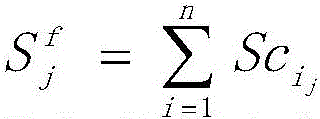
To obtain: wherein j belongs to { Da, R, E, A, Di }. That is, in this case, each weight in the parent node threat weight set is the maximum value of the weight in all the child node weight sets. Under the condition that subordinate child nodes are connected by OR logic, the threat weight of a father node can be represented by a formula
And (6) obtaining. That is, in this case, each weight in the parent threat weight is the sum of the class weights in all its child node weight sets. The DREAD classification evaluation system can be used for effectively describing the threat degree of each threat node in the threat tree of the system to be tested to the system, and although the description has certain subjectivity, the method can still be used as an effective basis for the safety evaluation of the system to be tested.
In addition to evaluating the severity of the damage possibly caused by the threats faced by the target system, the safety evaluation of the target system needs to evaluate the difficulty level generated by each threat and combine the test results to jointly draw a safety conclusion of the system to be tested. The embodiment analyzes and evaluates the difficulty level generated by each security threat of the tested system from two aspects of attack cost and attack probability.
The attack cost is the cost that an attacker needs to pay to implement a certain attack, and includes two types of physical cost and time cost. The physical cost refers to tangible capital invested by attackers to achieve an attack target, and mainly refers to special hardware equipment used in an attack process, such as Flash/ferroelectric read-write equipment, sniffers, protocol analysis equipment and the like. For the estimation of the physical cost, which involves a lot of factors, in order to simplify the model, a simple estimation of the physical cost will be made in the present context with the number of special hardware devices used. The time cost refers to the time that an attacker expects to take to achieve the attack goal, and obviously, the longer the attack takes, the higher the attack difficulty can be considered. In the security test, the time cost is often used to describe time-consuming attacks such as password cracking and ciphertext decryption, and for non-time-consuming attacks, the time cost is not generally calculated. Following this idea, for a non-time consuming attack, its time cost is considered to be 0; for time-consuming attacks, the time cost is determined according to the theoretical time consumption required for completing the attack.
In the measured system threat tree described as an AND/OR tree, the attack cost is in the form of a cost weight of the threat node. The cost weight value of each threat node in the threat tree is the same as the threat weight value, and the cost weight value of each threat node is determined according to the logical connection of the nodes under the jurisdiction. Setting n sub threat nodes under the jurisdiction of the current node, wherein the attack cost (including the attack cost of the node under the jurisdiction of physical cost AND time cost, AND under the condition that the nodes under the jurisdiction are connected by AND logic, the attack cost of the current node meets the relation
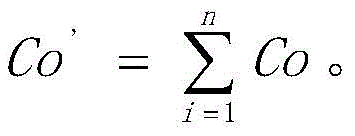
That is, under the condition that the subordinate nodes are in AND logical connection, the current node attack cost (including physical cost AND time cost) is the sum of the subordinate node attack costs. In the case where the subordinate nodes are logically connected by OR, the current node attack cost satisfies the relationship Co' max (Co)
i). That is, under the condition that the subordinate nodes are in OR logical connection, the current node attack cost (including physical and time costs) is the maximum value of the subordinate node attack costs. The attack cost can increase the difficulty of an attacker in attacking the tested system and provide a reference basis for security personnel in evaluating the threat degree of the attacker on the tested system, so that the method is one of important indexes for finally judging the safety of the tested system.
In conclusion, the method for detecting the safety of the internet of things provided by the embodiment improves the intelligent degree of the safety detection of the internet of things, can actively detect the safety loophole of the internet of things system, effectively reduces the attack threat, improves the system safety, and ensures the safety of the internet of things. The method for detecting the security of the internet of things provided by the embodiment can analyze and judge the attack threats which may occur, find out the threat vulnerabilities which may exist, and finally comprehensively evaluate the security performance of the mainstream RFID equipment in the communication process. The deep research of the project is beneficial to promoting the development of RFID security analysis test processing flow in the Internet of things industry, ensuring the safe and stable operation of key infrastructure, forming a safe, reliable and low-risk Internet of things product security analysis mode, and playing a demonstration role in the industry. In addition, the method can provide valuable reference for the research and application of the industrial and internet of things system in China, particularly the research and application in the aspects of RFID security and privacy system construction, risk assessment, standard formulation, product development and evaluation and the like in an intelligent manufacturing system.
Fig. 6 is a schematic structural diagram of a first embodiment of the internet of things security detection device of the present invention. As shown in fig. 6, the internet of things security detection device of the present invention includes: an acquisition module 601, a parsing module 602, an evaluation module 603, and an output module 604. The acquisition module 601 is used for acquiring a first communication signal between a reader and a tag in a first internet of things system; the analysis module 602 is configured to perform reverse analysis on the first communication signal to obtain attribute information of the first communication signal; the evaluation module 603 is configured to input the attribute information into the security evaluation model to obtain a security evaluation result of the first internet of things; the output module 604 is configured to output a security detection report corresponding to the security assessment result, where the security detection report includes a security risk level of the first internet of things system and/or a risk handling scheme of the first internet of things system.
The internet of things security detection device provided by this embodiment can be used to execute the internet of things security detection method shown in fig. 1, and the specific implementation manner and principle thereof are the same and are not described again.
Optionally, the internet of things security detection apparatus in the above embodiments further includes a processing module. The acquisition module is also used for acquiring a test instruction input by a user; the processing module is used for processing the attribute information of the first signal according to the test case corresponding to the test instruction.
Optionally, the attribute information of the first communication signal includes: potential destructiveness, reproducibility, availability, scope of influence, discoverability, physical cost of attack, time cost of attack, impact factor, and success rate of attack.
Optionally, the security threat model is a BP neural network; the BP neural network takes the attribute information of the first communication signal as input and outputs a safety evaluation result of the first Internet of things; wherein, the BP neural network has learned the safety evaluation results corresponding to the attribute information of different signals.
Optionally, the risk coping scheme may include: for the aerial frame, the anti-replay mechanism such as sequence number management is adopted; and the data stored locally is encrypted or obfuscated.
Optionally, the attack mode of the test case includes: dos attack, sniffing attack, counterfeiting attack, identity authentication test, data tampering, key acquisition, card cloning and other attack modes.
The internet of things safety detection device provided in the above embodiments can be used to execute the internet of things safety detection method provided in each of the above embodiments, and the specific implementation manner and principle thereof are the same and are not described again.
An embodiment of the present invention further provides an electronic device, including: a processor; and the number of the first and second groups,
a memory for storing executable instructions of the processor;
wherein the processor is configured to execute the method for detecting the security of the internet of things in any one of the above embodiments via executing the executable instructions.
An embodiment of the present invention further provides an internet of things security detection processing device, including:
the safety detection method of the internet of things comprises a memory, a processor and a computer program, wherein the computer program is stored in the memory, and the processor runs the computer program to execute the safety detection method of the internet of things in the embodiments.
An embodiment of the present invention further provides a storage medium, including:
the system comprises a readable storage medium and a computer program, wherein the computer program is stored on the readable storage medium and is used for realizing the internet of things security detection method in the embodiments.
An embodiment of the present invention further provides a program product, including:
a computer program (i.e., executing instructions) stored in a readable storage medium. The computer program can be read from a readable storage medium by at least one processor of the encoding device, and the computer program is executed by the at least one processor to enable the encoding device to implement the internet of things security detection method provided by the foregoing various embodiments.
Those of ordinary skill in the art will understand that: all or a portion of the steps of implementing the above-described method embodiments may be performed by hardware associated with program instructions. The program may be stored in a computer-readable storage medium. When executed, the program performs steps comprising the method embodiments described above; and the aforementioned storage medium includes: various media that can store program codes, such as ROM, RAM, magnetic or optical disks. The above description is only a preferred embodiment of the present invention, and is not intended to limit the present invention in any way, and any simple modification, equivalent change and modification made to the above embodiment according to the technical spirit of the present invention are still within the scope of the technical solution of the present invention.
Finally, it should be noted that: the above embodiments are only used to illustrate the technical solution of the present invention, and not to limit the same; while the invention has been described in detail and with reference to the foregoing embodiments, it will be understood by those skilled in the art that: the technical solutions described in the foregoing embodiments may still be modified, or some or all of the technical features may be equivalently replaced; and the modifications or the substitutions do not make the essence of the corresponding technical solutions depart from the scope of the technical solutions of the embodiments of the present invention.